LFGA Web
Authentication - Learning
The Portswigger Web Academy
Before you start
- In the Portswigger Web Academy you'll find the theoretical information and explanation, then you'll find a challenge, make sure to understand the information before you start the challenge.
- The theoretical information is such important as the challenge or practical part.
- Take your notes they are very important.
- Try to do everything by yourself, but remember that we are learning so feel free to see the solution and follow it, you'll learn a lot
- You are going to need Burpsuite, find the way to install it and research how to use it, the Academy will teach you how to use some functionalities of the tool. I recommend this video if you need some introduction: Burpsuite Basics (FREE Community Edition)
- Google is your friend.
Link: Authentication - Portswigger
After the activity
You now know:
- What is Authentication.
- The difference between authentication and authorization.
- How do authentication vulnerabilities arise.
- The impact of vulnerable authentication.
- Vulnerabilities in password-based login.
- Brute-force attacks (passwords and usernames).
- User enumeration.
- How to do an intruder sniper attack in Burpsuite.
- How to do an intruder pitchfork attack in Burpsuite.
- How to do an intruder cluster bomb attack in Burpsuite.
- How use Grep - Extract in an intruder attack in Burpsuite.
- How to bypass an IP-based brute-force protection using the X-Forwarded-For header.
- How to use the session handling rule editor.
- Use a macro in Burpsuite.
- Use the decoder.
- How to enumerate users via an account lock.
- Send multiple credentials per request.
- How HTTP basic authentication works.
- What are multi-factor authentication vulnerabilities.
- Bypass a two-factor authentication.
- Exploit a flawed two-factor verification logic.
- Bypass a 2FA authentication using a brute force attack.
- Brute-force a cookie to stay login.
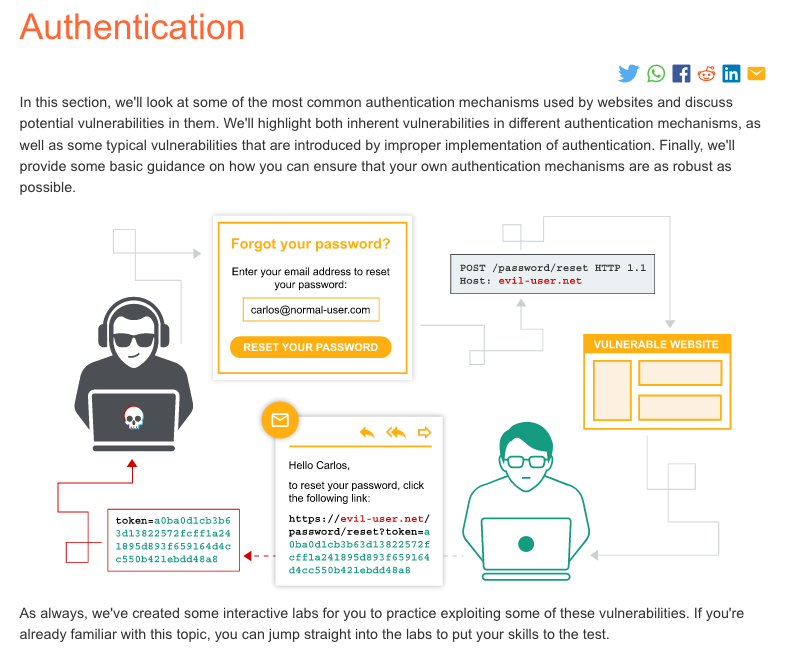
- Exploit a reset password functionality.
- Reset a password poisoning.
- Exploit the change password functionality.
Try Hack Me - Authentication
In Try Hack Me we are going to use the OWASP top ten room and we are going to do the day 2 (Broken Authentication) practical and theoretical part.
Room:
Sections:

Link:
OWASP Top 10Before the activity
- Follow the steps.
- Notes!.
After the activity
You now know:
- What are Brute force attacks.
- What is Use of weak credentials.
- What are Weak Session Cookies.
- Exploit a weak sanitized input.
That's all!
Let's go to the challenge section.