LFGA Web
XXE - Learning Section
The Portswigger Web Academy
The portswigger academy has a wonderful and complete course about XXE, we'll start here.
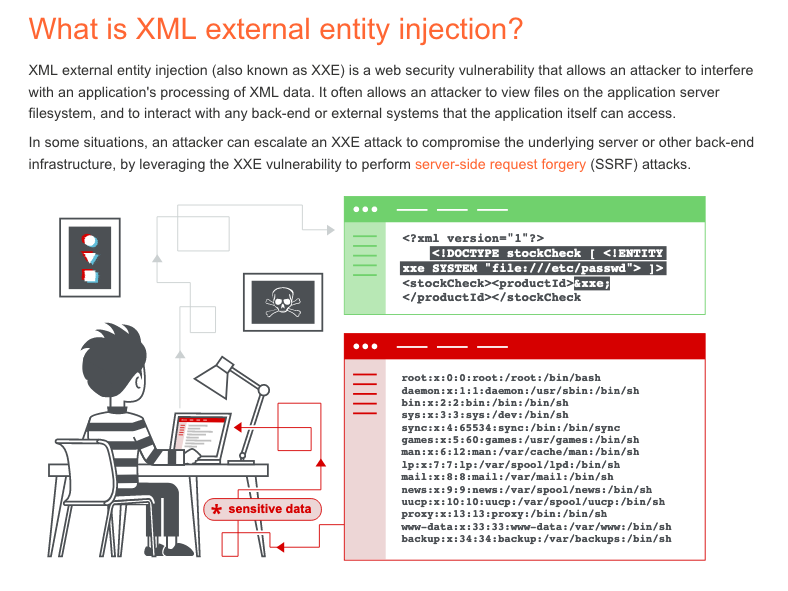
Before you start
- In the Portswigger Web Academy you'll find the theoretical information and explanation, then you'll find a challenge, make sure to understand the information before you start the challenge.
- The theoretical information is such important as the challenge or practical part.
- Take your notes they are very important.
- Try to do everything by yourself, but remember that we are learning so feel free to see the solution and follow it, you'll learn a lot
- Google is your friend.
- Some of the labs will require Burpsuite pro edition if you don't have it feel free to jump the lab, but remember the theoretical part is important.
Link: XXE - Portswigger
After the activity
You now know:
- What XML external entity injection is.
- How do XXE vulnerabilities arise.
- What XML is.
- What XML entities are.
- What a document type definition is.
- What XML custom entities are.
- What XML external entities are.
- Exploit XXE to retrieve files.
- Exploit XXE to perform SSRF attacks.
- Exploit blind XXE to retrieve data via error messages.
- Exploit blind XXE by repurposing a local DTD.
- What blind XXE vulnerabilities are.
- Perform XXE XInclude attacks.
- Perform XXE attacks via file upload.
- Perform XXE XXE attacks via modified content type.
Try Hack Me
Now let's just reinforce what we just learned. Let's get back to a room that we have used previously and focus on XXE. The room is: OWASP Top 10

And you have to do task 13, 14, 15 and 16.
Before you start
- This activity is like a reinforcement of what we already learned.
- If is necessary supplement your notes
After the activity
- You have already reviewed what an XML External Entity is.
- You have already reviewed what XML is.
- You have already reviewed what a Document Type Definition in XML is.
- You have already reviewed what an XXE payload is.
PayloadsAllTheThings
If you need alternatives or want to see different ways to exploit XXE you can always go to PayloadsAllTheThings XML External Entity - PayloadsAllTheThings

That's all for the learning section. The portswigger course is very complete so if you did everything right, you won't have any trouble in the challenge section, but there are still lots of variations in XXE vulnerability. Let's get to the challenge section!.